Data-Driven Risk Management: The Future is Here
The era of reactive risk management waiting for a crisis to occur before formulating a response is officially over.
Read MoreJuly 26, 2024
In today's competitive job market, organizations must ensure they are hiring the right candidates while mitigating risks associated with employment. A comprehensive background screening strategy is essential for verifying the credentials, experience, and integrity of potential employees. This document outlines the key components of an effective background screening strategy, including best practices, legal considerations, and the importance of integrating technology into the process.
Background screening involves the process of investigating a candidate's history, including their criminal record, employment history, education verification, and other relevant information. The goal is to provide employers with a clear picture of a candidate's qualifications and potential risks.
Before implementing a background screening process, organizations should define the scope based on the position being filled. Different roles may require different levels of scrutiny. For example, positions involving financial responsibilities may necessitate a more thorough check than entry-level roles.
Selecting a reputable background screening provider is crucial. Organizations should look for providers that comply with the Fair Credit Reporting Act (FCRA) and have a proven track record of accuracy and reliability. It's important to evaluate the provider's services, turnaround time, and customer support.
Before conducting any background checks, employers must obtain written consent from candidates. This not only complies with legal requirements but also fosters transparency and trust in the hiring process.
A comprehensive background screening should include:
Employers must be aware of and comply with federal, state, and local laws regarding background checks. This includes understanding the FCRA, Equal Employment Opportunity Commission (EEOC) guidelines, and any specific state regulations that may apply.
Leveraging technology can streamline the background screening process. Automated systems can help manage consent forms, track screening progress, and store results securely. Additionally, using software that integrates with applicant tracking systems can enhance efficiency.
Background screening policies should be reviewed and updated regularly to adapt to changes in laws, technology, and organizational needs. Continuous improvement ensures that the screening process remains effective and compliant.
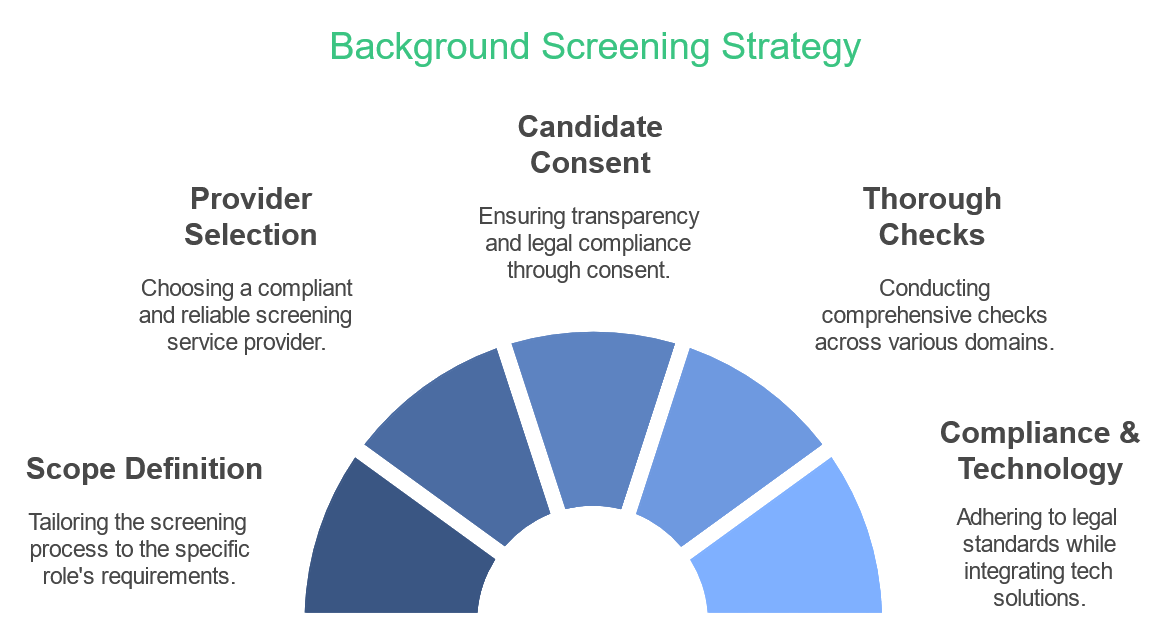
A comprehensive background screening strategy is vital for organizations aiming to make informed hiring decisions while minimizing risks. By defining the scope, choosing the right provider, obtaining consent, conducting thorough checks, ensuring compliance, integrating technology, and regularly reviewing policies, employers can build a robust screening process that supports their hiring goals and protects their organization.
Security Consulting
The era of reactive risk management waiting for a crisis to occur before formulating a response is officially over.
Read More
Security Consulting
For businesses in Nigeria and across the globe, understanding and mitigating physical risks has never been more critical.
Read More
Protective Intelligence
Should ordinary citizens take up arms to defend themselves? On the surface, it seems a simple, visceral answer to a complex problem.
Read More